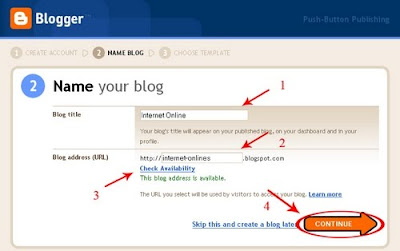
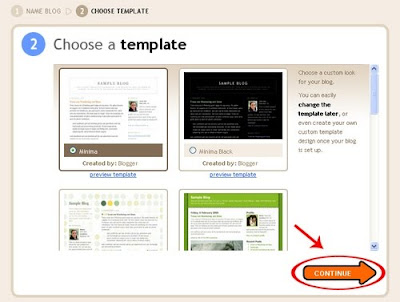
What’s this “Paid to Click” programs?
As what the phrase says these are programs where advertisers pay you after clicking or viewing their advertisements for about 10 - 30 seconds. Every successful clicking or viewing = $0.005 up to $0.02 credit to your account. Good PTC sites are probably the best way to make money on the internet and best of all they are legal and FREE to join. Paid to click is an easy way to make money online if you keep your advertising budget low. ere’s how it works in a nutshell: Advertisers need low cost advertising and they are willing to pay for the visitors.
Read More »»
As what the phrase says these are programs where advertisers pay you after clicking or viewing their advertisements for about 10 - 30 seconds. Every successful clicking or viewing = $0.005 up to $0.02 credit to your account. Good PTC sites are probably the best way to make money on the internet and best of all they are legal and FREE to join. Paid to click is an easy way to make money online if you keep your advertising budget low. ere’s how it works in a nutshell: Advertisers need low cost advertising and they are willing to pay for the visitors.
What is a PTC site?
PTC site programs are NOT a Autosurf, Multi-Level Marketing, Pyramid, Ponzi, Matrix or “Get Rich Quick” scheme.
PTC sites are new innovative, international and FREE English based services that allow advertisers to reach thousands of potential customers by displaying their ad on their “Surf Ads” page. An exact calculated percentage of all advertising revenue is paid to their members (that’s us!). PTC sites make money via advertising, other advertising sources throughout the website as well as earning through direct sponsorship of other members, just like a regular member does.
Is it free to join?
Absolutely yes! You don’t need to spend a single dime upon signing up or even if you are already earning. So there’s no reason not to join. No risk at all!
How do I earn?
You earn by just clicking and displaying the Ads for 10 - 30 seconds that can be found on your login page after signing up. 4 up to 8+ advertisements are available to click on each PTC site everyday. You will earn much more money if you refer the program to your other friends. You will also earn on every click they make so invite as many friends as you can after joining. You can earn $0.005 up to $0.01 per referral click.
Below is an example of your potential earnings based on averages:
• You click 10 ads per day = $0.10
• 20 referrals click 10 ads per day = $1.00
• Your daily earnings = $1.10
• Your weekly earnings = $7.70
• Your monthly earnings = $33.00
*) Reminder: Click & display the ads one at a time or one after the other in order for your earnings to be credited to you.
How do I get my earnings?
If you have already reached the minimum payout, you can now cash it out via PayPal or Alertpay. These are account-managing systems in the internet and are currently know
n to be the safest. After cashing out, login to your PayPal or Alertpay account and click the ‘withdraw’ feature so that your money will be transferred to your Bank or Debit Card. After that, you can now withdraw your money through accredited ATM machines.
PTC site programs are NOT a Autosurf, Multi-Level Marketing, Pyramid, Ponzi, Matrix or “Get Rich Quick” scheme.
PTC sites are new innovative, international and FREE English based services that allow advertisers to reach thousands of potential customers by displaying their ad on their “Surf Ads” page. An exact calculated percentage of all advertising revenue is paid to their members (that’s us!). PTC sites make money via advertising, other advertising sources throughout the website as well as earning through direct sponsorship of other members, just like a regular member does.
Is it free to join?
Absolutely yes! You don’t need to spend a single dime upon signing up or even if you are already earning. So there’s no reason not to join. No risk at all!
How do I earn?
You earn by just clicking and displaying the Ads for 10 - 30 seconds that can be found on your login page after signing up. 4 up to 8+ advertisements are available to click on each PTC site everyday. You will earn much more money if you refer the program to your other friends. You will also earn on every click they make so invite as many friends as you can after joining. You can earn $0.005 up to $0.01 per referral click.
Below is an example of your potential earnings based on averages:
• You click 10 ads per day = $0.10
• 20 referrals click 10 ads per day = $1.00
• Your daily earnings = $1.10
• Your weekly earnings = $7.70
• Your monthly earnings = $33.00
*) Reminder: Click & display the ads one at a time or one after the other in order for your earnings to be credited to you.
How do I get my earnings?
If you have already reached the minimum payout, you can now cash it out via PayPal or Alertpay. These are account-managing systems in the internet and are currently know
n to be the safest. After cashing out, login to your PayPal or Alertpay account and click the ‘withdraw’ feature so that your money will be transferred to your Bank or Debit Card. After that, you can now withdraw your money through accredited ATM machines.